- Home
- Acrobat
- Discussions
- Cannot get a "signature validated" with a Globalsi...
- Cannot get a "signature validated" with a Globalsi...
Copy link to clipboard
Copied
I have a document, correctly signed with a (higly expensive) GlobalSign hardware certificate plugged to a computer. GlobalSign is present in the Adobe's Trust List (Adobe Approved Trust List Members, Acrobat ), but still looks like it's not valid on Adobe Acrobat Pro DC for macOS:
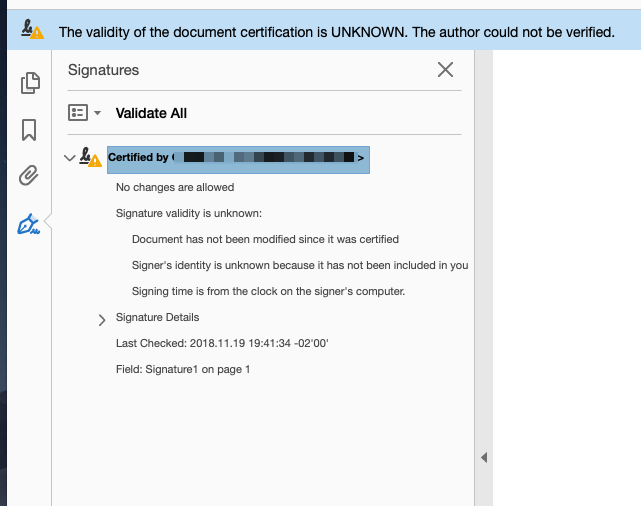
Adobe Acrobat Pro DC version 2019.008.20080
Architecture: x86_64
Build: 19.8.20080.306727
AGM: 4.30.81
CoolType: 5.14.5
JP2K: 1.2.2.41572
So, what is the problem here?
Thank you,
Antonio Carlos
Copy link to clipboard
Copied
Hello!
I’d like to thank you for using our product, and reassure that your clients don’t need to give any special trust to our root certificates when using up to date adobe programs on up to date machines.
This issue is resolvable with a few troubleshooting steps, as it is most likely based on an old token driver package that built an “incorrect” certificate chain upon issuance.
We want to check that the relevant, newest drivers for the token are on the signing machine. The current safenet version can be checked by opening the Safenet Client Tools program, and hitting the informational “i” at the very top. If found to be an older version (8.x, 9.x) please download the latest drivers from our support article linked below:
https://support.globalsign.com/customer/portal/articles/1698654
With the newest token program, you should
1. Initialize the token and
2. reissue your certificate using our portal, which will push out a new download link to install to the “fresh” token client. This will make sure the correct certificate chain and all its details are installed to the token correctly.
This should do the trick and make sure no special trust needs to be given by end users. We can help more directly with the process if you reach out to us at any of the mentioned avenues listed at the below link:
https://www.globalsign.com/en/company/contact/support/
With regards,
GlobalSign Marketing Team
Copy link to clipboard
Copied
Hi acribeiro,
As per the issue description mentioned above, you are facing issue when trying to validate the certificate for GlobalSign certificate, is that correct?
Could you try trusting the root of the certificate chain as the following thread suggests and check if that helps:
You may also visit the following forum threads discussing the similar issue:
Why is the validity of my digitally signed document displayed as unknown?
Let us know if you need any help.
Shivam
Copy link to clipboard
Copied
Hey Adorobat,
Thanks for taking time to answer.
What I want is my app to send a signed document to a client's user and make sure they will not call (me or my client) back telling me (nor my client) that the certificate we just send them is not valid, when they double click the file to see what's inside.
So, what you (that answer) are telling me is that, for that to happen, I'll have to tell all my client's users, which I have no control over, to make a procedure (of trusting a root certificate directly from the document) that Adobe Reader itself says is dangerous? Even though I got it from a (theoretically) Adobe trusted provider?

That really doesn't looks like a safe and secure procedure do execute, at all, not when we are dealing with signatures which were supposed to be trustable by themselves.
And, looks like I can just buy a $10 certificate online, tell them to do exactly the same (trust the root CA) and voilá!
What's the point of buying from that Adobe Approved Trust List?
And, sorry to go even lower, but I looks like that also works with signed certificates!

Thank you,
Antonio
Copy link to clipboard
Copied
Hello!
I’d like to thank you for using our product, and reassure that your clients don’t need to give any special trust to our root certificates when using up to date adobe programs on up to date machines.
This issue is resolvable with a few troubleshooting steps, as it is most likely based on an old token driver package that built an “incorrect” certificate chain upon issuance.
We want to check that the relevant, newest drivers for the token are on the signing machine. The current safenet version can be checked by opening the Safenet Client Tools program, and hitting the informational “i” at the very top. If found to be an older version (8.x, 9.x) please download the latest drivers from our support article linked below:
https://support.globalsign.com/customer/portal/articles/1698654
With the newest token program, you should
1. Initialize the token and
2. reissue your certificate using our portal, which will push out a new download link to install to the “fresh” token client. This will make sure the correct certificate chain and all its details are installed to the token correctly.
This should do the trick and make sure no special trust needs to be given by end users. We can help more directly with the process if you reach out to us at any of the mentioned avenues listed at the below link:
https://www.globalsign.com/en/company/contact/support/
With regards,
GlobalSign Marketing Team
Find more inspiration, events, and resources on the new Adobe Community
Explore Now