Signature is invalid - Invalid Policy Constraint - Certificate from EUTL
- May 13, 2021
- 2 replies
- 15974 views
Hello,
I have a digitally signed document with qualified certificate from EUTL - CA named "First certification authority, a.s." or https://www.ica.cz/.
As of today, signature with this certificate is showing as an Invalid, with error "Invalid Policy Constraint".
Version of my Acrobat Reader DC: 2021.001.20155
First, I tried is to turn off "load certificates from AATL server" and only left EUTL turned on in preferences, this did nothing, Acrobat is still showing source of trust obtained from AATL.
Second, I found this thread and it seems like in the end nobody solved it. https://community.adobe.com/t5/acrobat/previously-valid-signing-certificate-shows-invalid-policy-constraint-in-dc-2019/td-p/10573803
Since this is policy constraint error, here I share the policies from root cert. in chain.
I also attached signed file.
Multiple certificates from different persons are returning this error.
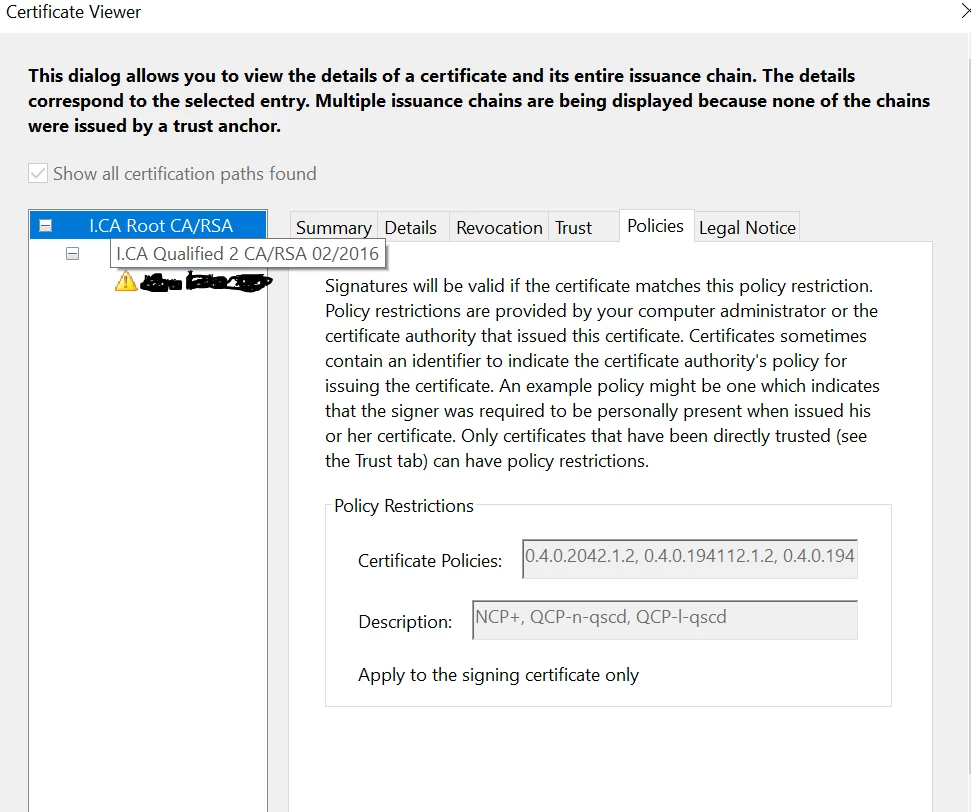
Could you give me some advice how to solve this?
Kind regards,
John

