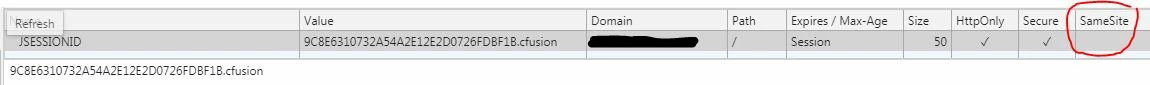
jsessionid and SameSite=None for ColdFusion 10
Hi, I am running ColdFusion10 Enterprise and we found two of our sites vulnerable to the Chrome80 update for SameSite cookies. I have "Use J2EE session variables" checked and Session Cookie Settings set for HTTPOnly. The issue is our main site iframes this supporting site in and we get console message "A cookie associated with a cross-site resource at *Domain Name Here* was set without the `SameSite` attribute. It has been blocked". Since these are different domains it doesn't work. I am trying to find out if there is a way to set that SameSite value to "none" for the jsessionid cookie. I tried a few things thru the Java and JVM settigs but nothing worked there and in fact actually hosed it up once and had to revert it. Any ideas/suggestions/solutions are greatly appreciated. Thanks.