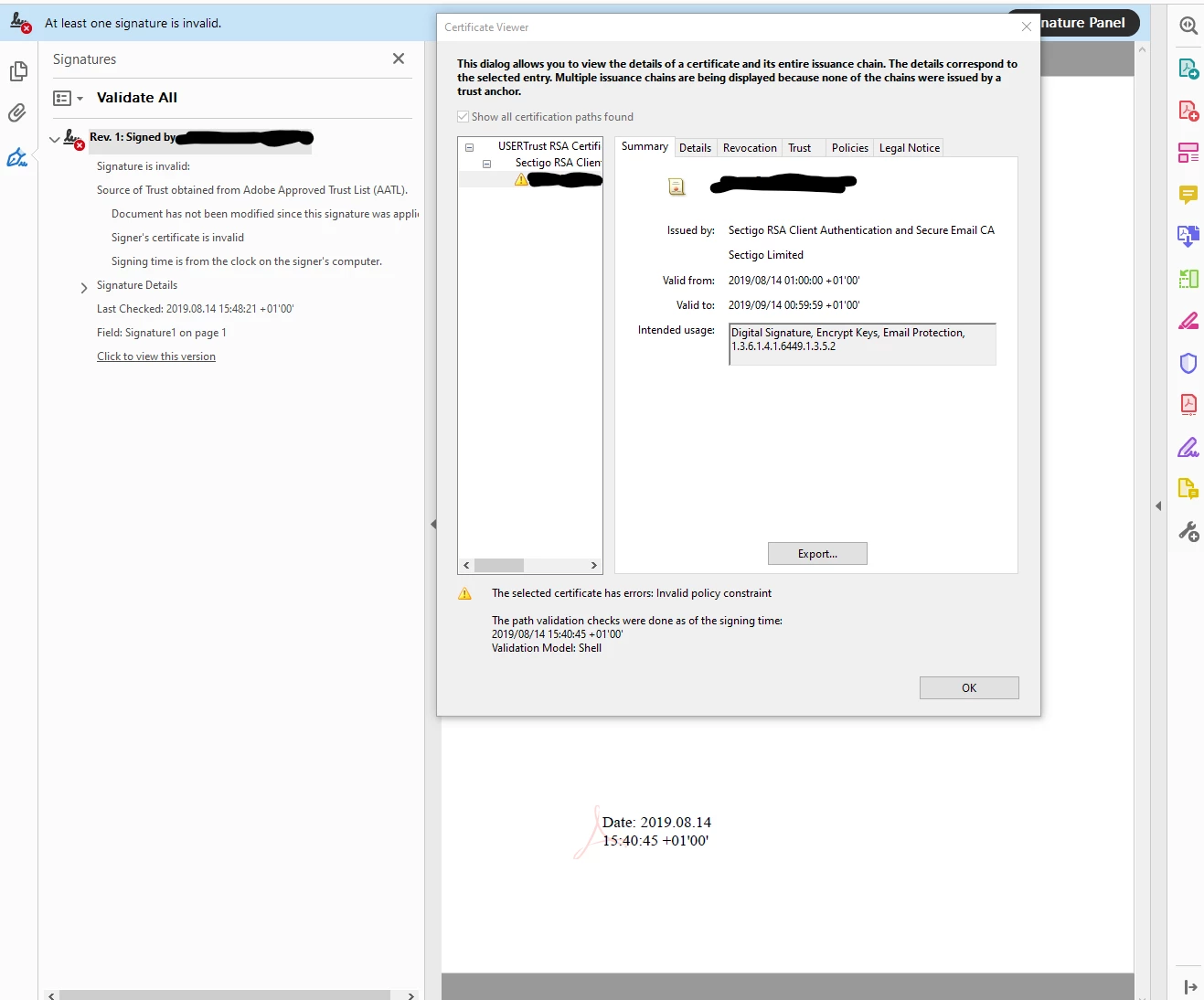
Previously valid signing certificate shows invalid policy constraint in DC 2019
We have previously been able to sign documents with certificates with the following intended usages: Digital Signature, Encrypt Keys, Email Protection, 1.3.6.1.4.1.6449.1.3.5.2
As per Steven.Madwin's response to Document signing requires code signing certificate this should be fine. However as of Acrobat Reader DC 2019 the signature is marked as invalid. The certificate path shows "Invalid policy constraint" for the issuing certificate paths and the signing certificate. The certificate we are using is issued by Sectigo and is AATL approved.
Has Acrobat become fussier about the types of certificates it will accept. If so what needs to be present in the certificate?