HTTP Response Splitting in CF2018
Hi, we recently had a security scan on one of our apps and we were dinged with "HTTP Response Splitting" issue. It occured on my .CFC pages. Below is what the testers performed on my CFC and the results.
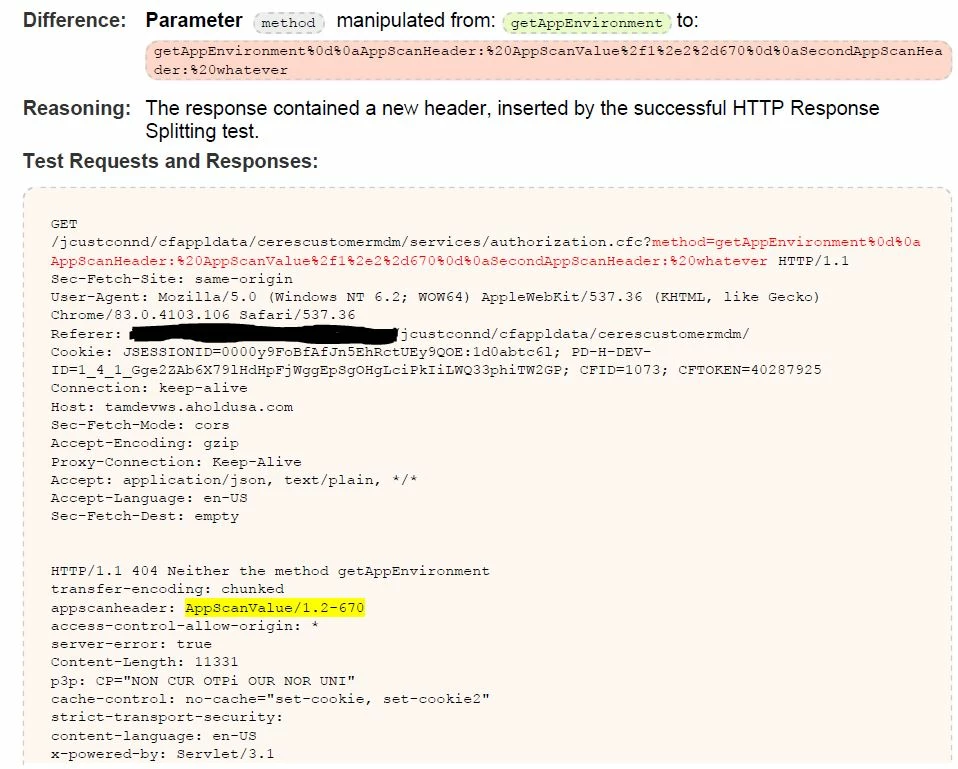
I am running CF2018 Enterprise 2018.0.09.318650. I was curious if anyone had any suggestions on how to remediate this. My first step was to make sure "Enable Global Script Protection" was checked in the cfadmin, which it is. From there I believe the neo-security.xml file can be updated to help prevent CRLF injection, not sure what that would look like. Quite honestly I am not sure if that is the best or proper method. I get a little leary messing with some of the CF underlying files. Anyone have any other or better ideas?
Thanks

