Secure connection, what to do?
My client sees the following warning when he logs into a website created by me. The site allows proprietary information to be viewed/used, but does not pose a threat if an unauthorised person gains access.
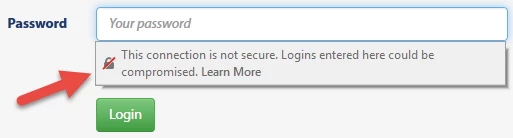
Info held in a database includes name, address, location, phone and email. According to the Privacy Act, this info may not be divulged.
Should the client invest in an SSL certificate? If so, which level? Any recommendations?



