Inspiring
May 20, 2022
Answered
NeoID (Brazil gov. A3 cloud certificate) does not work fine when signed on Acrobat (Pro/Reader)
- May 20, 2022
- 1 reply
- 3519 views
Hi team,
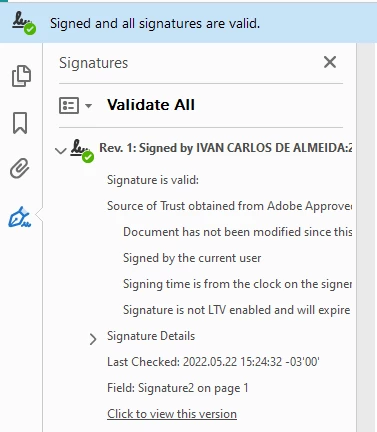
I am trying to sign document using my Adobe Acrobat DC Pro and it always reports that "the document has been altered or corrupted since the signature was applied".
The chain certificate is fine, and when certified using another application like PDF-XChange it validated fine on Adobe Acrobat. The problem is when sign it using Adobe Acrobat.
Please, how can we fix this issue?
Adobe Acrobat DC Pro version 2022.001.20117
Note: This "cloud" certificate works like any local certificate, when you sign it locally, instead of asking for a pin, it asks to confirm its 2FA prompt approval on a mobile app.
In attach:
screenshot "error signed by Adobe Acrobat DC Pro.png"
screenshot "pass signed by PDF-XChange.png"
Thanks a lot and regards